Anonymous No More: Countering the Gray Zone Threat
Introduction
Adversary state actors successfully leverage gray zone activities and exploit their relative anonymity at the unclassified level to counter the conventional advantages of the United States and our allies. Our current agreements, policies, and procedures are inadequate to oppose the gray zone activities in competition; however, our current doctrine and tactics are more than sufficient to defeat these gray zone activities in crisis and conflict. During two recent North Atlantic Treaty Organization (NATO) exercises, the V Corps G-2 successfully used identity intelligence to remove adversary intelligence operatives’ anonymity and defeat the gray zone network in the rear area.
The National Intelligence Council describes gray zone activities as “coercion and subversion . . . below what constitutes armed conflict but outside the bounds of historically legitimate statecraft.”1 Writing in 2023, Major Ryan Barkholder described the gray zone as “an operational environment in which actors use multiple instruments of power to pursue political-security objectives through graduated activities that are more fervent than steady-state competition, exploit ambiguity, and fall below the threshold of conventional warfare.”2 Deniability is critical to the success of this strategy; attribution risks escalation and effective response by the United States and her allies.3
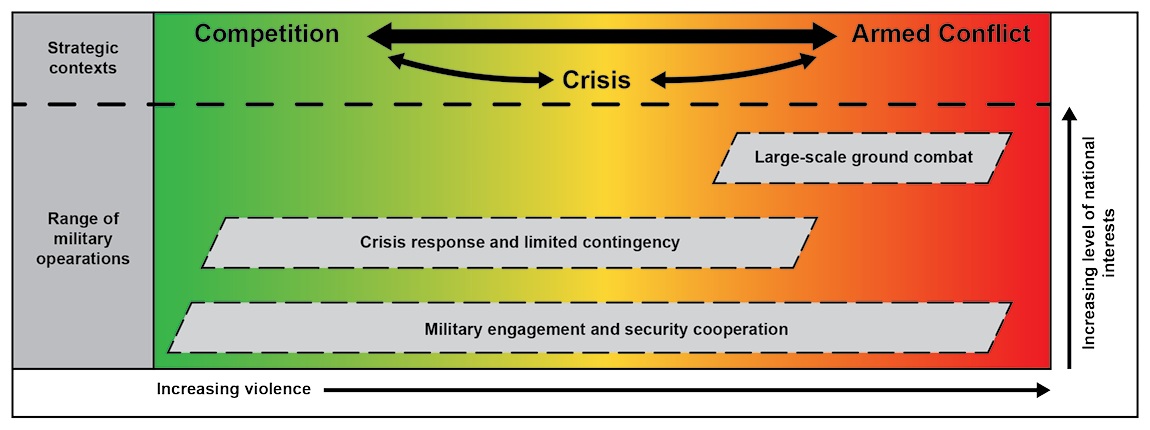
Specific gray zone tactics vary depending on their strategic context. In competition, sustained information operations and using proxy political organizations to counter U.S. access to the targeted region define gray zone threats.5 In crisis, gray zone tactics elevate to include covert support to organized criminal gangs, sabotage, and increased cyberspace attacks.6 In conflict, gray zone activities shift to a hybrid threat model operating in the tactical, operational, and strategic rear areas, seeking to undercut the legitimacy of U.S. forces, disaggregate our alliances, remove our will to fight, and disrupt our momentum.7
Recently, Russia has expanded its gray zone campaign in Europe. Within the last year, Russia has been accused of—
- Infiltrating water treatment plants in Finland, Sweden, and Germany.
- Detonating arson devices on DHL facilities and aircraft in Germany and the United Kingdom.
- Sponsoring arson attacks in Lithuania and Latvia.
- Conducting small unmanned aircraft system (sUAS) overflights of critical infrastructure in Sweden and Germany.
- Attempting to assassinate the Chief Executive Officer of German arms manufacturer Rheinmettal.9
Polish authorities closed the Russian Consulate in Poznan as a result of several incidents in Poland.10 Countless other events across Europe remain unattributed, preventing an effective, unified allied response.
When faced with a similar attribution gap in the late 1990s, the U.S. Army developed the concept of identity intelligence. Used successfully during the Global War on Terrorism, identity intelligence is defined by Joint Publication 2-0, Joint Intelligence, as “the intelligence resulting from the processing of identity attributes” and is used to deny adversaries anonymity.11 Identity intelligence that leverages biometrics-enabled intelligence (BEI) can remove Russia’s anonymity in gray zone sabotage efforts and enable the United States and our allies to defeat adversarial actors. BEI uses the measurable anatomical, physiological, biographical, and behavioral characteristics of an individual (i.e., their biometrics) in combination with other information to connect an individual to a significant activity.12
In two recent NATO exercises, the V Corps G-2 used two separate elements of BEI to identify, counter, and defeat gray zone actors in crisis and conflict. During Avenger Triad 24, V Corps used behavioral and biographical characteristics to find, fix, and defeat a state-sponsored threat cell operating in the V Corps rear area. During Northern Spirit 24, V Corps worked alongside NATO allies using anatomical characteristics to identify gray zone actors—including threat actor proxies and transnational criminal organizations—and establish NATO’s first international biometric-enabled watchlist (BEWL).
Avenger Triad 24: Using Identity Intelligence to Secure the Corps Rear Area
Avenger Triad 24 was a multinational, multicomponent, multi-corps NATO exercise based on a 2025 large-scale combat scenario in the European theater. V Corps was one of six corps, participating alongside the Multinational Corps Northeast, the 1st German-Netherlands Corps, the 2nd Polish Corps, the NATO Rapid Deployable Corps-Spain, and the Allied Rapid Reaction Corps. The authors led a small team, including an embedded French officer, in the intelligence section of the V Corps rear command post.
The corps rear command post is responsible for planning and directing sustainment, terrain management, movement control, and security of the corps rear area.14 During Avenger Triad, the primary threats to these responsibilities were divided between traditional special purpose forces (SPF) conducting reconnaissance and enabling long-range precision fires and gray zone actors employing cyberspace attacks, crowd-sourced intelligence, improvised explosive devices (IEDs) on critical national infrastructure, and protests to halt each corps momentum.
Using conventional intelligence preparation of the operational environment and intelligence analysis techniques, the V Corps G-2, along with the expeditionary sustainment command G-2, the maneuver enhancement brigade S-2, and the military police brigade S-2, was able to identify potential staging locations for the SPF battalion operating in the V Corps area. Employing collateral collection on assets returning to base in conjunction with exploiting downed tactical unmanned aircraft systems and captured tactical unmanned aircraft system waypoints and routine military police patrols, V Corps could find, fix, and finish the SPF battalion within 48 hours. After sharing these tactics, techniques, and procedures (TTPs) with the Multinational Corps Northeast and the 2nd Polish Corps, V Corps identified a second SPF battalion moving from the Multinational Corps Northeast’s area of operations into the V Corps area of operations. Close coordination with the assigned maneuver enhancement brigade S-2 and combat aviation brigade S-2 enabled V Corps to ambush this massed SPF formation as they entered the V Corps area of operations and neutralized the SPF threat.
Countering the gray zone cell proved more difficult, especially at a releasable level. While the 2nd Polish Corps did provide some releasable human intelligence reporting on the gray zone cell, it was often delayed and incomplete. Instead, V Corps utilized behavioral characteristics to identify several gray zone social media entities, enabling V Corps to use its organic open-source intelligence cell to develop a fully releasable network diagram for tracking the gray zone cell in near-real time. As a result of this TTP, V Corps successfully disrupted an attempted crowd-sourced intelligence collection scheme across the theater and rapidly dispatched maneuver enhancement brigade and military police patrols to gray zone threat locations. These actions ultimately denied the adversary an opportunity to target critical national infrastructure and helped tailor the V Corps messaging campaign. Being able to attribute seemingly mundane events like train derailments, criminal distributed denial of service attacks, and organized protests to this gray zone cell denied the enemy freedom of maneuver and rendered their gray zone efforts insignificant.
Critical to the defeat of this gray zone cell was the ability to share threat information with adjacent multinational corps and host nation agencies. During Avenger Triad, the gray zone cell consistently moved between the corps’ rear areas to avoid detection and exploited the seams between the corps’ areas of operations. Sharing the updated threat assessments and TTPs between adjacent corps enabled an accurate common intelligence picture, preventing the gray zone cell from taking advantage of corps seams. Additionally, having publicly releasable intelligence enabled V Corps to work alongside the Polish Territorial Defense Forces (and, by proxy, host nation law enforcement) to attribute gray zone actions to the enemy. This attribution and subsequent publication of the threat to the general public increased the sensors V Corps had on the gray zone cell. They directly defeated the crowd-sourced intelligence collection attempt and undercut gray zone actor anti-NATO messaging.
Northern Spirit 24
Northern Spirit is an annual NATO BEI exercise. In 2024, Northern Spirit was nested with Ardent Defender, an annual NATO explosive ordnance disposal (EOD) exercise, to assess new NATO identity intelligence doctrine. The common exercise scenario simulated a NATO task force assisting a nation in crisis attempting to counter a state-sponsored gray zone actor. EOD personnel and enhanced field exploitation teams responded to and exploited incidents, sending captured exploitable material to a Canadian lab. Biometric samples collected by the lab were processed through the NATO Automated Biometric Identification System (ABIS) and six additional national ABISs. Once an individual was identified, the biometric match report was sent to the identity intelligence cell for fusion with all-source reporting and BEWL nomination. During the exercise, a separate legal advisor cell worked through potential issues with NATO, national, and international laws, policies, and procedures. Northern Spirit was the first NATO exercise to simulate a NATO-led BEWL. Both Northern Spirit and Ardent Defender assumed a biometric sharing agreement between the NATO countries and the host nation government.
V Corps provided four personnel to Northern Spirit/Ardent Defender 24: one EOD officer (enhanced field exploitation team observer), one human intelligence warrant officer (ABIS observer), one lawyer (legal advisor participant), and one intelligence officer (identity intelligence participant).
The now obsolete Army Techniques Publication 2-22.82, Biometrics-Enabled Intelligence, dated November 2015, heavily influenced the NATO doctrine for BEI and identity intelligence, laid out in NATO Standardization Agreement (STANAG) 6515, Countering Threat Anonymity: Biometrics in Support of NATO Operations and Intelligence. In contrast to U.S. doctrine, NATO does not retain any biometric data; instead, data collected during NATO operations remains with the member or partner country that originally collected the data.15 The NATO ABIS serves as a transaction manager, temporarily transmitting the search to the federated national ABIS, screening the results against national release limits, and transmitting the screened results back to the original requestor. While this doctrine preserves national equities, it results in a fragmented picture of the adversary.16 NATO identity intelligence doctrine does not recognize behavioral attributes as part of identification.17 Until this exercise, NATO also opted not to maintain a BEWL, relying instead on member nations to establish bilateral BEWL sharing agreements. During Northern Spirit, NATO used a BEWL for the first time as a test, starting with two enrollment categories: Person of Interest and Terrorist/Insurgent. There is currently no published NATO STANAG on BEWLs.
The Northern Spirit threat consisted of a state-sponsored ethnic separatist movement and a transnational criminal organization serving as a state proxy. Both threat organizations sought to undermine the legitimacy of a Western-aligned host nation government and received training, lethal support, and amplified information operations from their state sponsor, a neighbor of the targeted government. Among the threat tactics observed were one-way attack UASs, complex IEDs, vehicle-borne IEDs, disinformation campaigns, commercial sUAS reconnaissance of NATO facilities, criminal vandalism, and modified commercial drones to deploy lethal munitions.
Through Northern Spirit, the international identity intelligence cell successfully used BEI derived from captured exploitable material collected by the Ardent Defender enhanced field exploitation teams, exploited through a Canadian-led multinational lab, and evaluated through six national ABIS databases to build out threat networks and to nominate several threat personas, insider threats, and persons of interest to the NATO BEWL. The current NATO BEWL doctrine, including the nomination process and BEWL categories, has proved insufficient. During the exercise, the identity intelligence and legal advisor cells collaborated on defining additional watch list categories (including force protection categories). Still, national limitations prevented NATO from adopting all of the 33 current U.S. watch categories.
The current NATO exploitation doctrine and TTPs have proved sufficient for collecting biometrics during the exercise. However, especially with sUAS, BEI failed to remove the anonymity of threat actors on a first-time encounter; only with routine patrols, host nation security force engagement, and field biometric enrollment was the identity intelligence cell able to identify the sUAS reconnaissance cell. Other gray zone TTPs (e.g., arson, IEDs, sabotage) were easier to attribute after the NATO task force and host nation law enforcement established an agreement to share biometric data.
Left unaddressed in Northern Spirit was the application of BEI to the targeting process and how to integrate that targeting process with host nation law enforcement for a judicial solution to gray zone activity. Future doctrine and exercises integrating national and international law enforcement organizations should be developed.
Conclusion: An Imperfect Defense
The experiences of V Corps at Avenger Triad and Northern Spirit highlight successful identity intelligence TTPs to remove the anonymity of adversarial gray zone actions in crisis and conflict. Open-source intelligence enabled V Corps to produce publicly available reports, which inoculated the population against gray zone messaging and disrupted gray zone actors. Cross-corps communication and integrating host nation law enforcement denied the adversary physical, procedural, and policy-based seams for exploitation. Northern Spirit highlighted a way forward for a combined NATO BEWL that balances national caveats while enabling a better understanding of common threats.
While these TTPs proved successful in crisis and conflict, they are not currently deployable in competition. Historically, the U.S. treats gray zone actions in competition as a law enforcement matter, collected and supported primarily by U.S. special operations forces. Like the terrorism threat in the early 1990s, this policy gap remains exploitable by adversarial actors as V Corps and regional NATO allies regularly witness along the eastern flank. Continued simulation of gray zone threats in exercises, which add to the complexity of current steady-state conventional threats, will help build a shared understanding between allied formations and interagency partners. Additionally, continued U.S. and NATO exercises incorporating identity intelligence will help identify, test, and work through potential policy differences, international agreement gaps, and procedural interoperability to narrow the adversary’s window of anonymity.
Endnotes
1. Office of the Director of National Intelligence, National Intelligence Council, Conflict in the Gray Zone: A Prevailing Geopolitical Dynamic Through 2030, July 2024, https://www.dni.gov/files/ODNI/documents/assessments/NIC-Unclassified-Conflict-In-The-Gray-Zone-July2024.pdf.
2, Ryan Barkholder, “Tackling Russian Gray Zone Approaches in the Post-Cold War Era,” Journal of Advanced Military Studies 14, no. 2 (2023): 158, https://doi.org/10.21140/mcuj.20231402008.
3. Department of the Army, Army Techniques Publication (ATP) 7-100.1, Russian Tactics (Washington, DC: U.S. Government Publishing Office [GPO], 29 February 2024), 1-4. Change 1 was issued on 23 April 2024.
4. Figure adapted from Figure 1-3, Department of the Army, Field Manual 3-0 Operations (Washington, DC: U.S. GPO, 01 October 2022), 1-14.
5. Department of the Army, ATP 7-100.1, Russian Tactics, 2-7.
6. Ibid.
7. Ibid., 2-1 and 2-7.
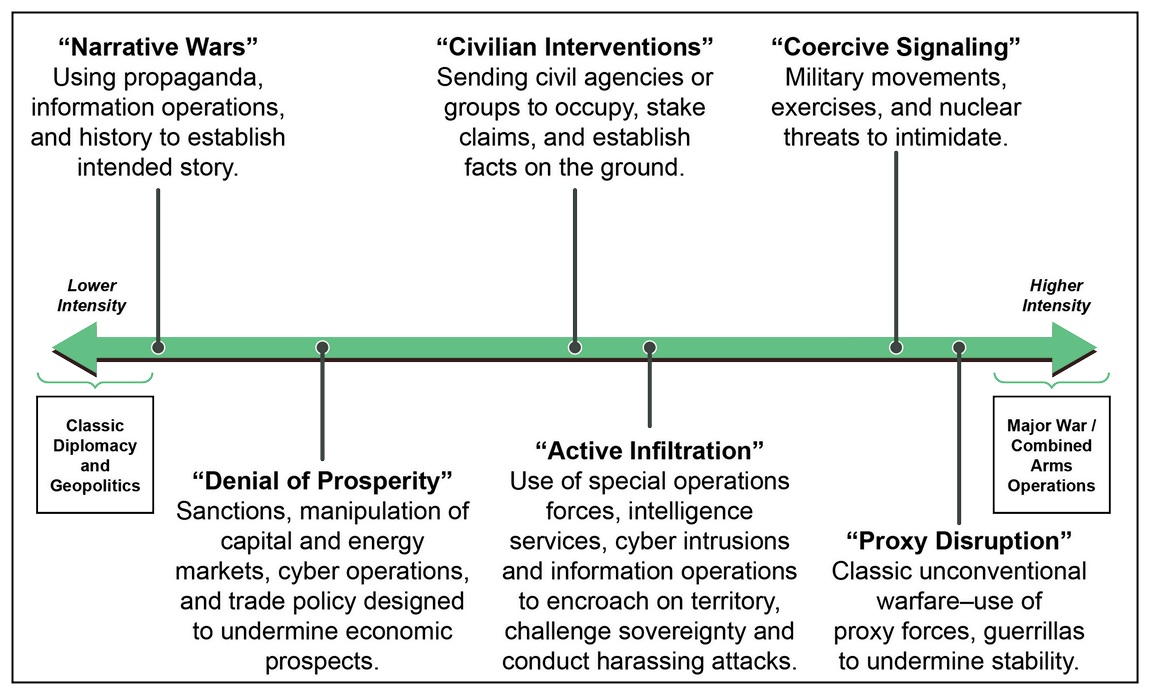
8. Figure 5-2 from Michael J. Mazarr, “Understanding Gray Zone Conflict,” in Mastering the Gray Zone: Understanding A Changing Era of Conflict (Carlisle, PA: Strategic Studies Institute, U.S. Army War College, 2015), 60. http://www.jstor.org/stable/resrep12018.9.
9. Peter Apps, “Russia’s Suspected Sabotage Campaign Steps Up in Europe,” Reuters, October 20, 2024, www.reuters.com/world/russias-suspected-sabotage-campaign-steps-up-europe-2024-10-21/.
10. Natalia Ojewska, “Poland to Close Russian Consulate Over Sabotage Claims.” Bloomberg, October 22, 2024, https://www.bloomberg.com/news/articles/2024-10-22/poland-to-close-russian-consulate-in-poznan-over-sabotage-claims.
11. Office of the Chairman of the Joint Chiefs of Staff, Joint Publication (JP) 2-0, Joint Intelligence (Washington, DC: The Joint Staff, 26 May 2022), GL 14. Change 1 was issued 05 July 2024.
12. Ibid., D-5.
13. Ibid., D-8-D-9.
14. Department of the Army, ATP 2-19.3, Corps and Division Intelligence Techniques (Washington, DC: U.S. GPO, 08 March 2023), 2-3.
15. North Atlantic Treaty Organization (NATO), Standardization Agreement 6515, Countering Threat Anonymity: Biometrics in Support of NATO Operations and Intelligence (Brussels, Belgium: NATO Standardization Office, 23 February 2016), 3-1.
16. Ibid., 2-5.
17. Ibid., 5-9.
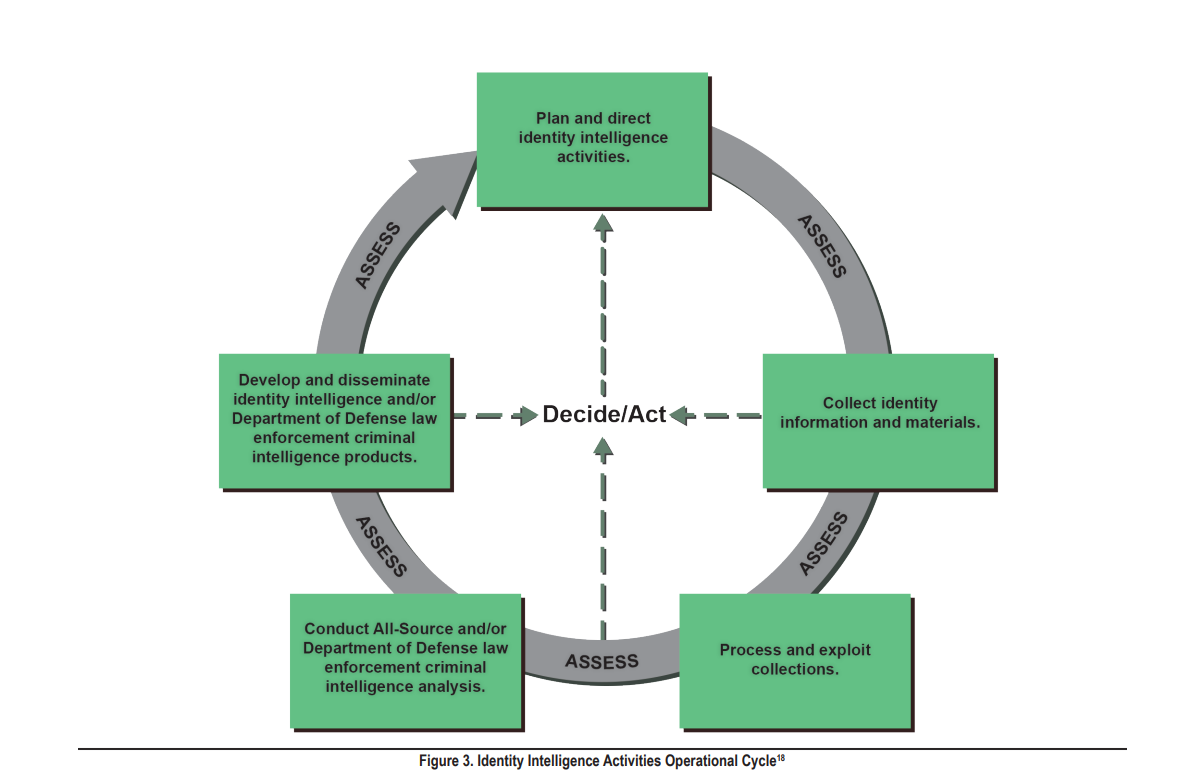
18. Figure adapted from Figure D-2., Joint Chiefs of Staff, JP 2-0, Joint Intelligence, D-7.
LTC H. Eric Perez-Rivera is the V Corps G-2 Chief of Operations. He previously served in the North Atlantic Treaty Organization Supreme Headquarters Allied Powers Europe J-2X and in multiple intelligence positions at the tactical, operational, and strategic levels over the last 28 years.
CPT Wade Allen serves as a G-2 Operations Officer for V Corps at Fort Knox, KY. He previously served as a company commander for two separate headquarters companies as well as serving as a Patriot Battalion S-2.